The below lab follows on from "Part 1 Active Directory Migration ADMT". All user accounts have now been migrated from source domain Silverwater.local the to destination Rhodes.local.
This part of the migration focuses upon the mailbox migration. For this step we plan to use the Microsoft Exchange Server Migration Wizard (MAILMIG.EXE). Using this wizard simplifies the migration and ensures each migrated user receives their full mailbox. The alternative approach would be to export \ import PST file from source to destination Exchange Servers, which would be a time consuming and without scripting a manual process.
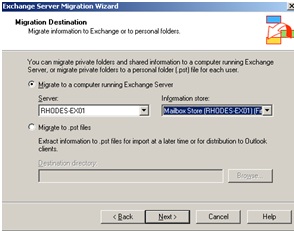
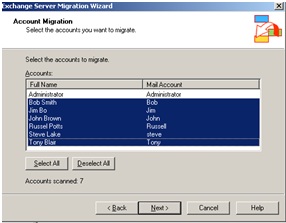
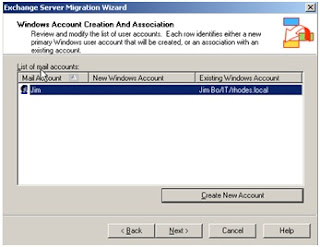
Earlier in the migration chose to retained the users SID, doing so now allows us align the source mailbox with the destination user account across the separate forests. Note if the user SID was not migrated with the user acount across the forests then this process would not allow us the link the mailbox with the user account (as shown in step 5), therefore the only option would be leverage the Exmerg tool.
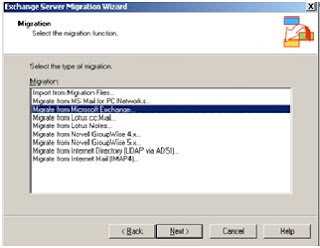
You can only migrate mailboxes from the source server if the source server is not part of the same Exchange 2003 organization as the server that is running the Migration Wizard.
What is the difference between Intraorganizational- and Interorganizational Migration?
Intraorganizational migration: The mailboxes will be migrated between Exchange Servers in ONE Exchange Organization.
Interorganizational migration: The mailboxes will be migrated between Exchange Servers in DIFFERENT Exchange Organizations.
The below lists the steps involved in migrating mailboxes from Silverwater.local to Rhode.local.au
You can start the Migration Wizard by clicking Start – Microsoft Exchange – Deployment – Migration Wizard (MAILMIG.EXE).
1. Run the Exchange Server Migration Wizard from the Rhodes Exchange Server
You can only migrate mailboxes from the source server if the source server is not part of the same Exchange 2003 organization as the server that is running the Migration Wizard.
What is the difference between Intraorganizational- and Interorganizational Migration?
Intraorganizational migration: The mailboxes will be migrated between Exchange Servers in ONE Exchange Organization.
Interorganizational migration: The mailboxes will be migrated between Exchange Servers in DIFFERENT Exchange Organizations.
The below lists the steps involved in migrating mailboxes from Silverwater.local to Rhode.local.au
You can start the Migration Wizard by clicking Start – Microsoft Exchange – Deployment – Migration Wizard (MAILMIG.EXE).
1. Run the Exchange Server Migration Wizard from the Rhodes Exchange Server